Biometrics refers to the automated recognition of individuals based on their unique physiological or behavioral characteristics. Biometrics involves the collection and analysis of biometric data, such as fingerprints, iris patterns, facial features, voice, or gait, to establish a biometric ID for authentication or identification purposes.
Biometrics is significant in various domains due to its potential to enhance security, convenience, and efficiency. Biometrics provides a more reliable and accurate method of identification compared to traditional authentication methods such as passwords or PINs by relying on distinctive individual traits. Biometric authentication offers a higher level of security by utilizing unique biological or behavioral characteristics that are difficult to forge or replicate.
The advantages of biometrics include increased security, as it is difficult for impostors to fake or steal biometric traits. Biometric authentication offers non-transferable and non-replicable identification, reducing the risks associated with lost or stolen credentials. Biometrics enhances the user experience by providing convenient and quick access to secured areas or resources. It eliminates the need to remember complex passwords and reduces the time required for manual authentication processes.
There are disadvantages to consider. Biometric systems rely on the collection and storage of sensitive biometric data, which raises concerns about privacy and data protection. Biometric data, such as fingerprints or iris patterns, stolen or misused if not properly secured. There is a risk of false acceptances or rejections, where the system incorrectly match or reject legitimate individuals, leading to inconvenience or security vulnerabilities. The deployment and maintenance of biometric systems are costly and require specialized equipment and infrastructure.
What Is Biometrics?
Biometrics is the science and technology of studying and measuring a person’s unique physical or mental traits. People are found, identified, and their identities are checked by using the traits. Biometric systems read and analyze things such as fingerprints, facial patterns, eye or retina patterns, voiceprints, hand geometry, gait, or behavioral traits including typing patterns or signature dynamics.
Biometric systems are meant to be a safe and reliable way to identify people because it is hard to fake or copy the biometric data that is collected. They are used for many things, namely controlling entry to physical spaces, authenticating computer systems and online platforms, controlling immigration and border crossings, law enforcement, and forensic investigations.
The concept of biometrics dates back several centuries, but its modern development began in the late 19th and early 20th centuries. The French police officer Alphonse Bertillon developed a system called anthropometry in the late 19th century. The system involved measuring various physical characteristics of individuals, such as height, arm length, and head circumference, for the purpose of criminal identification. Anthropometry had limitations, although it was used for identification.
Sir Francis Galton, a cousin of Charles Darwin, conducted research on fingerprints in the late 19th century. Galton established the uniqueness and permanence of fingerprints, leading to the development of fingerprint identification. Fingerprint identification became the first widely adopted biometric technique, with the establishment of automated fingerprint identification systems (AFIS) in the 1970s.
Researchers began exploring automated face recognition techniques in the 1960s. Significant progress in face recognition technology was made in the 1990s and 2000s, because of the advancements in computer vision and pattern recognition algorithms. Face recognition is now widely used in various applications, including surveillance systems and smartphone authentication.
Other modalities gained prominence as biometrics advanced. Iris recognition technology was introduced, allowing for the identification of individuals based on unique patterns in their irises, in the 1980s. Voice recognition systems developed during the same time, enabling identification based on vocal characteristics. Hand geometry, retina scans, vein patterns, and behavioral biometrics such as gait analysis and keystroke dynamics have been explored and utilized in biometric systems.
The field of biometrics continues to evolve with advancements in technology, such as machine learning and artificial intelligence. The advancements improve the accuracy, security, and efficiency of biometric systems, leading to their widespread adoption across various domains.
How Does Biometric Authentication Work?
Biometric authentication uses a number of steps to make sure that a person is who they say they are. Biometric authentication starts with the registration process, in which the person’s unique biometric data, such as fingerprints, face, iris, or voice, is recorded and turned into a reference template. A database stores the code safely.
They connect with the biometric system by giving a biometric trait when a person needs to be authenticated. The system takes real biometric data, such as a fingerprint scan, a picture of the face, or a sample of the voice. The collected data is processed to pull out the important features that make a person’s biometric trait stand out from others. The characteristics are turned into a digital copy or biometric code.
The system compares the new fingerprint template to the reference templates that have already been saved in the database. Different mathematical algorithms are used to figure out how similar two templates are and what amount of match they are. A choice is made based on whether the match is more than a certain number.
Authentication is considered successful if the amount of match is higher than the threshold, and the person is let in or verified. Authentication is rejected and entry is denied if the match is below the threshold. The fingerprint system tells the result, which is usually “Access Granted” or “Access Denied,” along with other information, like how sure it is that they are the right person.
Biometric systems typically store mathematical models or templates of the biometric data instead of the data itself to protect privacy and safety. It makes it so that even if the saved templates are stolen, it is very hard to get the original biometric information back. Encryption and other security measures are used to keep the saved templates safe and stop people from getting to them without permission. The steps make up the flow of biometric identification, which is a safe and reliable way to check someone’s identity.
What Is the Importance of Biometrics?
Biometrics is important in a wide range of real-world situations because it makes things safer, easier, and more efficient. One significant part is that it makes people feel safer. Biometric traits offer a higher level of security than traditional methods like passwords or PINs because they are unique to each person and hard to copy. It makes sure that only authorized people get into sensitive systems, physical places, or personal data. It helps stop identity theft, unauthorized access, and fraudulent activities.
Biometrics makes sure that the right person is being identified. Using unique physical or behavioral traits, such as fingerprints, face patterns, or iris scans, enables to identify and verify people with confidence. Accuracy is especially helpful in areas like law enforcement, border control, and forensic investigations, where accurate identification is important for keeping the public safe and stopping crime.
Biometric registration makes things easy and smooth for the user. Users no longer have to remember complicated passwords or keep track of them. They do not have to carry around actual tokens. The identification process is quick, simple, and easy to use because biometric traits are natural to each person. Applications such as unlocking smartphones, accessing banking services, or entering secured facilities are streamlined and simplified through biometric authentication, enhancing user satisfaction and productivity.
Biometric devices save both time and money when it comes to how well they work. They make it easier for administrators to keep track of passwords, access cards, or PINs for numerous users. Biometrics are used to automate the process of verifying an individual’s name. It improves operational efficiency and reduces human error. They get rid of the need to change passwords or get new access cards often, which saves money and makes better use of resources.
Biometrics helps stop scams and hold people accountable. Biometrics provides a strong audit trail by uniquely linking people to their actions. It makes it hard for people to deny that they were involved in certain transactions or activities. Accountability is useful in financial activities, e-government, healthcare, and other areas where accurate identification and traceability are needed.
Biometrics works well with other technologies, such as mobile devices, wearables, and Internet of Things (IoT) products. It allows adding biometric identification to a wide range of apps and services. Biometrics are used to make mobile payments safer, get into smart homes, verify online transactions, and even track health in a way that is unique.
What Are the Applications of Biometrics?
Biometrics is used in many areas and industries because it is used to identify people in a safe and accurate way. Access control is a popular use of biometrics. It is used a lot to control who gets into places like buildings, offices, and restricted areas. Access control systems make sure that only approved people get in by using biometric features like fingerprints, facial recognition, or iris scans. It improves security and stops people from getting in without permission.
Biometrics is used a lot in law enforcement and investigative investigations. Fingerprint recognition has been used to solve crimes, find suspects, and match prints found at crime scenes for more than 100 years. Face recognition and eye scanning are being used more and more by police to identify and track suspects.
Biometrics are important when it comes to border control and immigration. Biometric systems like e-passports and face recognition are used to quickly identify and process travelers at border crossings and immigration checkpoints. It improves security and cuts down on identity fraud.
Biometrics are used in the financial services industry to make sure transactions are safe and stop scams. Biometric authentication is built into mobile banking apps, ATMs, and payment systems. It makes it easy and safe for customers to access their accounts and approve transactions.
Biometrics are used in healthcare to identify patients and give only authorized people access to their medical details. Biometric technologies help stop medical identity theft, make sure that patients are correctly identified, and make healthcare services more efficient and accurate overall.
Biometrics are used to check someone’s name in a number of situations, such as when registering to vote, getting a government ID, and using national databases. Duplicate registrations are avoided, names are checked, and the integrity of the identification process is made sure of by using biometric authentication.
Biometrics are used by time and attendance tracking systems to track employees’ presence and keep track of their work hours. The systems correctly track employee attendance, get rid of human mistakes, and stop people from keeping time without permission by using biometric features like fingerprints, hand geometry, or facial recognition.
Biometrics are built into mobile devices and apps so that users are verified and have safe access. Fingerprint sensors, facial recognition, and iris scanning let users open their devices, log in to apps, and approve secure transactions. It makes mobile interactions safer and more convenient.
Biometrics are used in aviation security systems to improve customer screening and security at airports. Face recognition and fingerprint reading are used to identify passengers, help with boarding, and match people on watch lists.
Biometrics are used to keep the Internet of Things (IoT) environment safe. Users’ access to linked devices, data, and networks is kept private and secure by adding biometric authentication to IoT systems.
The examples show how biometrics are used in many fields. They are used in more places, like smart homes, retail, hospitality, and more, where secure and easy identification and authentication are needed as biometric technologies keep getting better.
What Are the Applications of Biometrics in Law Enforcement?
Biometrics is a big part of a lot of different ways that law enforcement uses it. Biometrics gives them useful tools and ways to improve investigations, identification, and public safety as a whole. One important use of biometrics is to help identify suspects. For example, fingerprint identification is used to match latent fingerprints found at crime scenes with fingerprints of known people. It helps identify suspects and cut down leads. Biometric databases and automated fingerprint identification systems (AFIS) help manage criminal databases. It is because they make it easy to compare and match biometric data to find criminals, help with investigations, and share information between different jurisdictions.
Biometrics helps with biometric forensics by letting fingerprints, palm prints, and tracks found at crime scenes be analyzed and compared to biometric databases. The process helps find connections between suspects and specific crimes, making it easier to identify people and link them to the scene of a crime. Biometric proof is used in court and helps the prosecution prove their case.
Police are using facial recognition technology more and more to identify suspects and keep an eye on public areas. Surveillance systems that have face recognition compare live video footage to databases of known people to help find suspects or people of interest. The technology is helpful for finding lost people or figuring out who people are in high-security places.
Eye recognition, which is known for being accurate and reliable, is used to record and match each person’s unique eye pattern. The technology is used by law enforcement when fingerprint identification is hard because there are no useful prints or latent fingerprints.
Law enforcement uses speech recognition systems to analyze voices and figure out who is talking. Forensic voice analysis helps make sure that voice recordings are real, that people are identified by their voiceprints, and that voice evidence in criminal cases is reliable.
The result is actionable intelligence when biometrics are combined with other intelligence and research data. They find patterns, connections, and links between people, criminal activities, and groups when law enforcement agencies look at biometric data alongside other sources of information. It helps with crime prevention and police work that is based on information.
They take unique data like fingerprints or pictures of people’s faces to identify and verify people in real-time when police officers are out in the field with mobile devices. Mobile biometrics make it easy to identify suspects quickly, which speeds up reaction times and makes operations more efficient.
The uses of biometrics in law enforcement show how important it is for helping with cases, making it easier to identify people, and making the public safer as a whole. Biometric technologies make it easier for law enforcement to find and keep track of suspects, link people to crimes, and use strong intelligence to stop crimes before they happen.
What Are the Potential Applications of Biometrics in Healthcare?
The potential applications of biometrics in healthcare are seen in its practical uses. Biometrics changes how patients are identified, how access is controlled, and how care is given. Biometric traits such as fingerprints, palm prints, or iris scans make it easier to match patients with their medical data. It is one of the most critical uses of biometrics. It cuts down on medical mistakes, stops identity theft, and makes patients safer.
Biometrics is a key part of keeping electronic health data (EHR) safe. Biometric authentication lets healthcare workers get into patient records safely, keeping sensitive medical information private and safe. Biometrics makes it harder to get into EHRs and protects patient info.
Biometrics helps keep patients safe by making sure the right medicines are given to the right people in medication control. Biometric identification helps match patients with their medication profiles, which lowers the chance of medication mistakes and improves the general health of patients.
Biometrics is used to make a big difference in remote patient tracking. Biometric tools, like heart rate monitors and sleep trackers, give real-time information about a person’s body that is used to keep an eye on them from afar. The information is used to keep track of a patient’s health, spot any problems, and act quickly when needed.
Patient portals have biometric authentication built in, which gives patients safe access to their personal health information, scheduling of appointments, and contact with their healthcare providers. Patient portals make entry easier, improve data security, and encourage patients to take an active role in managing their own healthcare by using biometrics.
Biometrics helps quickly and accurately identify people who are not able to talk in an emergency. Biometric characteristics like fingerprints or facial recognition help doctors quickly recognize patients, look up their medical history, and give them the right care at the right time.
Biometrics makes blood transfusions safer by making sure the patient is who they say they are and that the right blood products are used. Doctors and nurses make sure that patients get the right blood type and reduce the chance that they have a bad response by using biometric identification.
Biometrics helps make sure that participants are correctly identified and that the right information is collected in clinical trials and studies. Biometric authentication helps stop participant fraud, keeps data accurate, and speeds up trial processes. It makes study results more reliable and efficient.
Biometrics make healthcare facilities safer by controlling who get into restricted places. Only people who are supposed to be there get into labs, pharmacies, or private patient areas in a quick and safe way by using biometrics. It makes it less likely that someone to get in without permission and keeps private resources safe.
Biometric technologies make it easier for healthcare providers to identify patients, keep health data safe, and improve the quality of care overall. The uses of biometrics in healthcare show how it improves patient safety, speeds up processes, makes data more secure, and makes healthcare more personalized and effective.
How Does Ai Strengthen the Cybersecurity of Biometric Systems?
AI is a key part of making biometric systems more secure because it does things like to find threats, stop spoofing, provide continuous identification, analyze user behavior, stop fraud, provide adaptive security, and protect privacy.
Biometric systems look at a huge amount of data to find trends and outliers that are signs of security risks with the help of AI algorithms. Anti-spoofing techniques use AI to learn from a big set of real and fake samples, which lets them tell the difference between real and fake biometric traits.
AI algorithms used for continuous authentication make sure that the person is there and is real by monitoring and analyzing biometric data in real-time. AI-based study of user behavior creates a baseline of normal behavior, which makes it to spot unusual or suspicious behavior.
AI helps stop fraud by analyzing data from many sources and looking for signs of scams. It makes it to change security measures by changing parameters in real-time and better threat detection based on new data and patterns.
AI protects the privacy of its users by using things like biometric template protection, which makes sure that saved templates are not turned around to get back to the original biometric data. AI in cybersecurity improves the security of biometric systems, making them more resistant to cyber threats and making sure that biometric identification processes are honest, private, and reliable through the features.
What Are the Different Types of Biometric Identifiers?
Biometric systems utilize various types of biometric identifiers to establish the identity of individuals. Biometric identifiers include fingerprint, face, iris, retina, voice, hand geometry, vein pattern, signature, gait analysis, and keystrokes.
The unique patterns and ridges on each person’s fingers are read by fingerprint biometrics. The common way has a high level of accuracy and is used for many things, from law enforcement to smartphone authentication.
Face recognition uses things like the distance between the eyes, the shape of the nose, and the shape of the chin to identify people. It is often used in things like surveillance systems, access control, and mobile device identification.
The complex patterns of the iris, the colored part of the eye that surrounds the pupil, are read by technology that reads the iris. The method is accurate and is used in situations where reliable identification is important because each person’s eye pattern is stable and unique.
Retina scanning includes taking pictures of the unique patterns of blood vessels at the back of the eye. The method is mostly used in high-security situations and needs special equipment.
Voice recognition uses the unique tone, pitch, and speech rhythms of a person’s voice to figure out who they are. It is regularly used in voice-controlled gadgets and authentication systems that work over the phone.
Hand geometry biometrics measures and studies the size and shape of a person’s hand, such as the length and width of the fingers and the shape of the palm.
Vein pattern recognition records the unique patterns of blood vessels under the skin, usually in the hand or finger. It gives a form of biometric identification that is very exact and safe.
Signature recognition looks at how a person writes, how hard they press on the pen, and how they move the pen across the paper. It is often used to verify legal papers and money transactions.
Gait analysis looks at how a person walks and how they move, such as the length of their steps and how they stand. It is used for apps that require continuous authentication and surveillance.
Keystroke dynamics measure a person’s typing speed, timing, and trends of key presses. It is used for ongoing authentication or as an extra factor in systems that use more than one factor to prove the person’s identity.
Each type of biometric identification has its own advantages and disadvantages, as well as different uses. The choice of identifier relies on things like how accurate it is, how easy it is to use, and what the application needs. Biometric systems use the different identifiers to provide safe and effective ways to identify people in many situations.
What Is the Purpose of Biometric Technology?
The purpose of biometric technology is to provide a safe and accurate way to identify and prove people based on their unique physical or behavioral traits. Biometrics is a way to find out and prove someone’s identity in different situations and applications.
One of the main goals of fingerprint technology is to improve security by making it more accurate and reliable than traditional methods like passwords or PINs. Biometric traits, like a person’s fingerprints, face, eye, or voice, are unique to each person and hard to fake or copy. It makes it harder for someone to get in without permission or steal someone’s identity.
Biometric technology makes things easier and better for the user by getting rid of the need to remember complicated passwords or carry real tokens. People quickly and easily prove their identity with fingerprints, which improves the user experience and increases productivity by using their biometric traits.
Biometric technology helps stop identity theft and fraud by letting people be correctly identified and linked to their actions. It makes things easier and more efficient by getting rid of the manual work involved in managing passwords and making identification, authentication, and access control faster and better. Biometrics helps with accountability and audibility by leaving a record of activity, transactions, or access to important systems or resources that are followed and checked.
What Are the Advantages of Using Biometrics for Authentication?
Listed below are the Advantages of Using Biometrics for Authentication.
- Increased Security: Biometrics provide a higher level of security compared to traditional authentication methods like passwords or PINs. Biometric traits are unique to individuals and difficult to replicate, making it extremely challenging for unauthorized individuals to gain access.
- Non-Transferable and Non-Replicable: Biometric traits are inherent to individuals and are not transferred or shared like passwords or access cards. It eliminates the risk of unauthorized use by someone else, enhancing security.
- Enhanced User Experience: Biometric authentication offers a seamless and user-friendly experience. Users no longer need to remember or manage complex passwords, improving convenience and reducing the likelihood of authentication-related issues.
- Auditability and Accountability: Biometric authentication creates a robust audit trail that links individuals to their actions. It enhances accountability and provides an invaluable tool for auditing and investigations, allowing organizations to track and verify user activities.
- Reduction in Fraud and Identity Theft: Biometrics significantly reduces the risk of fraud and identity theft. It is difficult for malicious actors to replicate biometric traits, minimizing the chances of unauthorized access or fraudulent transactions.
- Integration with Other Technologies: Biometric systems are easily integrated with other technologies, such as access control systems, surveillance systems, or mobile devices. It allows for seamless integration into existing infrastructure, enhancing overall security and usability.
- Versatility: Biometric authentication is applied across various domains and applications, including physical access control, logical access control, financial transactions, healthcare, and more. It offers versatility in its application, catering to diverse security requirements.
- Scalability: Biometric systems scale to accommodate large user populations, making them suitable for organizations of all sizes. They efficiently handle authentication for a vast number of users without compromising security or performance.
- Reduced Reliance on Passwords: Biometric authentication reduces the reliance on passwords, which are often weak or prone to being forgotten or stolen. It reduces the vulnerability associated with password-based authentication methods.
- Enhanced Convenience: Biometric authentication provides a convenient and quick way to verify identity. Users easily authenticate themselves by presenting their biometric traits, eliminating the need to memorize or carry additional authentication credentials.

1. Increased Security
Increased security means that there is a higher level of protection against fraud or unauthorized entry. Biometrics is a big part of making the world a safer place because it gives people a strong way to prove who they are based on their unique physical or mental traits.
Biometric traits, such as fingerprints, face, iris, and voice, are unique to each person. It is very rare that an unauthorized person uses someone else’s biometric traits to get in. Biometric systems use advanced anti-spoofing techniques to find and stop efforts to commit fraud. The methods look at different parts of the biometric trait to tell the difference between real and fake samples. It makes sure that only real biometric traits are used for identification.
The fact that biological traits are not shared or stolen like passwords or access cards does add an extra level of security. Biometric authentication is used as well with other things, like a PIN or a smart card, to form a multifactor authentication method that makes security even stronger.
Encryption and other data security methods make sure that biometric data is kept and sent safely. It lowers the risk of unauthorized access or data breaches. Biometrics offer more security because they are more accurate, harder to steal or lose, better at catching fraud, easier to use, and easier to check and account for.
2. Non-Transferable and Non-Replicable
Non-transferable and non-replicable are key characteristics of biometric traits. Non-transferable means that a person’s biological traits are not given to or taken from another person. Biometric traits are unique to each person and are not used by anyone else to get in without permission. It is hard to copy or fake biological traits, which is what “non-replicable” means. It is very hard to make a copy of someone’s biometrics that are exactly the same. It is rare that someone without permission to use someone else’s biometrics to impersonate them.
Biological systems use the fact that biological traits are not changed or copied to make people safer. A person’s biometric traits are taken note of and turned into a digital pattern or reference that is specific to them during the registration process. It is compared to the reference file that has been saved when the person shows their biometric trait to be authenticated. The system looks at the presented biometric trait and compares it to the registered template to see if they match. Entry is either granted or denied if they do not match.
The benefits of biometrics for non-transferable and non-replicable characteristics are significant. Biometrics are a good way to check someone’s identity because they use unique characteristics that are hard to copy or share. It makes it less likely that someone uses the information without permission or steals the name.
It is hard for bad people to fake or copy someone’s biometrics due to the fact that biometric features are not copied. It makes fraud and impersonation attempt much less likely. Biometric traits that are not shared or copied improve access control systems by making it easier to tell who someone is and lowering the risk of illegal entry or data breaches.
Biometrics protect privacy better than passwords or access cards because biometric traits are not easily tied to a person’s name or shared like passwords or access cards. Lastly, the fact that biometrics are not shared or copied makes it easier for users because they do not have to remember or carry around extra authentication details.
3. Enhanced User Experience
Enhanced user experience refers to an improved and user-friendly interaction between individuals and biometric systems during the authentication process. Biometric authentication makes the process easier because users do not have to remember and keep track of complicated passwords or carry real tokens.
Users quickly and easily verify their identities by showing their biological traits. It makes the process easy and quick. Biometric systems offer quick and easy identification. Users verify their identity in a matter of seconds, which reduces wait times and makes the user experience smooth.
Biometrics makes users satisfied and less frustrated by getting rid of common problems with passwords, like forgetting them or having to change them often. Biometric authentication uses well-known parts of people, like fingerprints or facial recognition, to create a natural and easy way to communicate. It makes it easier and more comfortable to use because the customer is already used to it.
Biometrics makes it easier to get into systems or applications because it does not have to do extra things like look for access cards or type in passwords. The streamlined process makes things easier for users and makes them happier generally.
Biometrics offers ease, seamless integration into different devices and apps, user-friendly interfaces, less authentication fatigue, and a better mix between security and usability for a better user experience.
4. Auditability and Accountability
Auditability and accountability are important parts of biometric systems that make sure the authentication process is safe and open. Auditability means that a system track and records events or actions so that they are looked at or checked later. Accountability means that people are responsible for their actions and choices and must answer for them. Biometrics uses things like audit trails, access control logs, and system tracking to put the ideas into practice.
Biometric systems create full audit trails that include timestamps, the exact biometric traits used, and the results of authentication attempts. The audit trails keep a thorough record of what users do. It lets organizations track and confirm user actions, looks into incidents, and, if necessary, do forensic analysis.
Access control logs work with biometric systems to record user access events, which are used to check for compliance, find oddities, or track down attempts to get in without permission. Real-time system monitoring lets to keep an eye on performance, a user trying to log in, and security breaches. It sends out alerts when it finds patterns or events that do not make sense and need to be looked into.
Biometrics help keep track of who did what by letting users be identified by their unique physical or behavioral traits. The exact identification links people to the specific things they do or transactions they make. It makes people more accountable. Biometric audit trails are very helpful for forensic investigations, putting together timelines, finding potential threats, and providing proof for legal or disciplinary actions in cases of security incidents or breaches.
Biometric systems help companies meet compliance and regulatory requirements by leaving audit trails and access control logs. It makes the authentication process transparent and accountable. Biometric authentication works as a deterrent, making people more responsible for their actions and discouraging unauthorized access or fraud.
Biometrics makes it easier to do audits and hold people accountable by making thorough audit trails, access control logs, and system monitoring. The benefits include better tracking and proof of what users do, help with forensic investigations, compliance with rules, and stopping people from getting in without permission. The features help make the authentication process more safe and clear, making sure that users are held responsible for their actions and making it easier to keep track of and control system activities.
5. Reduction in Fraud and Identity Theft
Reduction in fraud and identity theft refers to the prevention or mitigation of fraudulent activities and unauthorized use of someone’s identity. Biometrics is a key part of it because it uses unique and non-replicable biometric traits, uses anti-spoofing methods, and makes it attainable to use multiple factors of authentication.
Biometric traits, like a person’s fingerprints, face, eye, or voice, are unique to each person and hard to copy or fake. Biometric systems greatly reduce the chance that someone tries to commit theft by using a fake or stolen identity by using the traits to verify a person’s identity.
Advanced anti-spoofing methods look at different parts of the biological trait to tell the difference between real and fake samples. It adds another layer of security. Biometric authentication is combined with other factors, like a PIN or a smart card, to form a multifactor authentication method that makes it harder for fraudsters to get unauthorized access.
Continuous authentication looks at biometric trends in real-time. It helps find differences that are signs of fraud. Biometric systems work with fraud-detection algorithms to look for trends and find fraud in real-time. It sends out alerts so that actions are taken right away.
Biometrics helps cut down on fraud and identity theft by making it easier to identify people, preventing fraud because biometric traits are unique, increasing security, reducing the financial losses that come with fraudulent transactions, and protecting a person’s reputation by lowering the risk of fraud.
6. Integration with Other Technologies
Integration with other technologies means putting biometric systems together with other technologies or systems that work well with them to improve their usefulness, security, and user experience. The integration enables people to use biometric authentication successfully in a larger ecosystem of apps, devices, or infrastructure. It works by making sure that biometric systems and other components or systems work together and are compatible with each other.
It is usually done through standard protocols, APIs, or SDKs. Biometrics works with integration by integrating with access control systems for physical security, with mobile devices for easy access to applications and services. Integration work as well with identity management platforms for streamlined user identification and provisioning, with surveillance systems for real-time biometric recognition, and with multifactor authentication solutions for increased security. The user experience, efficiency, scalability, and freedom, when biometrics are combined with other technologies, improve security. They provide complete security solutions.
The integration allows individuals to use biometric authentication in a way that is smooth and consistent. It lets organizations use the best parts of different systems to improve overall security and usefulness.
7. Versatility
Versatility means that biometric authentication is used and works well in a wide range of situations, applications, or settings in biometrics. It is because fingerprint systems are flexible and work with different platforms, technologies, and security needs. Biometric features like fingerprints, face, iris, and voice are captured and processed in a standard way. It makes different systems and apps work together without any problems.
Biometrics are flexible because they allow multi-modal biometrics, which includes fingerprint, face, and voice recognition, among others. It lets groups choose the best modality for their needs and gives them the freedom to work around people’s preferences or limitations. Biometric systems also work with other platforms and technologies, like mobile devices, access control systems, identity management platforms, and monitoring systems. It allows for cross-platform integration. It makes sure that biometric authentication is used on a wide range of devices, apps, and settings without any problems.
There are many ways that sensors help with flexibility. Biometric authentication is flexible, so it is used in different situations. It is used to control access, verify identity, and authorize transactions in a safe and easy way. Another benefit is that biometrics offer a consistent and easy way to authenticate users, no matter what program or device they are using.
Biometrics simplifies identity management by providing a unified and interoperable identification solution. It makes the process less complicated and reduces the amount of work that needs to be done by administrators. Biometric authentication is used in many ways, which makes it a strong way to protect against illegal access, fraud, or identity theft. It is because biometric traits are unique and hard to be copied. Biometrics help companies in different industries meet compliance and regulatory requirements because they are flexible and adjusted to fit specific rules and guidelines.
Biometrics are versatile because they work with different types of biometrics, integrated across platforms, used in different businesses, and scaled to fit different user populations. Organizations use biometric authentication as a flexible and effective solution in a wide range of areas and use cases. It provides adaptability, a simpler user experience, efficient identity management, increased security, and compliance with regulatory requirements.
8. Scalability
Scalability in biometrics means that a system handles more users, transactions, and requests without affecting its performance, security, or usefulness. It involves making the system work well enough to handle a growing number of users and login requests, making sure that authentication works smoothly and reliably even when there are a lot of them.
Scalability in biometrics is achieved by improving the system’s hardware, software, and network design. It means using powerful computers, distributed processing, and cloud-based solutions to handle large amounts of biometric data and authentication requests.
Biometric algorithms and software are designed to handle biometric data quickly and efficiently so that processing times and resource use are kept to a minimum. The distributed design allows for parallel processing and load balancing. It makes sure that resources are used efficiently and that there is enough capacity to meet rising demand. Biometric systems are easily added to current infrastructure, like access control systems or identity management platforms, without causing problems or slowing things down.
Biometrics has a lot of perks when it comes to scalability. Biometric systems easily handle more users, so companies add more users without having to worry about authentication delays or bottlenecks. Scalable systems make the best use of their resources, making sure that authentication processes are quick and effective even when there are a lot of users. It keeps the user experience smooth.
Biometric solutions that are scaled up or down give organizations the freedom to add more devices, applications, or places to the system as needed. It makes sure that the system grows to meet changing needs without affecting its speed or security. Scalable biometric solutions save money because they make the most of the investments and do not need major hardware or infrastructure updates as the number of users grows.
Biometric systems that are scaled up make sure that identification processes keep up with growing user numbers and needs. Biometric solutions handle a growing number of users, use resources efficiently, give the system room to grow, and be cost-effective by optimizing hardware infrastructure, processing algorithms, and adopting a distributed design. It lets companies scale their biometric authentication systems in a way that works well, ensuring that authentication processes are reliable and efficient as the number of users grows.
9. Reduced Reliance on Passwords
Reduced reliance on passwords means that people are using biometric authentication and other more secure and easy-to-use alternatives to standard password-based authentication methods more and more. The change is meant to fix the problems and risks that come with passwords, like weak or easy-to-guess passwords, reusing passwords, and the chance of password theft or illegal access.
Biometric authentication needs to be used as a main or secondary authentication factor for less reliance on passwords to work. People prove they are who they say they are without just using passwords. They use their fingerprints, face, eyes, or voice. Biometric security is a safer and more convenient way to log in than using a password. It does by using physical or behavioral traits that are hard to copy or fake.
Biometrics work with less reliance on passwords because they get rid of security holes caused by passwords, improve security, make things easier for users, and allow multifactor authentication. Biometric identity gets rid of the issues that come with passwords, like weak passwords or using the same password more than once. People do not have to make and remember complicated passwords with biometrics. It makes the authentication process safer.
Biometric features are unique to each person, which makes it very hard for illegal people to copy or fake them. Biometric identity is more secure than passwords because it relies on the fact that each person’s biometric traits are unique and are not copied.
Biometric authentication is easier and easier to use than passwords. Users no longer have to remember and keep track of a bunch of different passwords for different systems or apps. They easily prove their identity by showing their genetic traits, which makes the user experience smooth and easy.
Biometric authentication is paired with other forms of authentication, like a PIN or a smart card, to make a multifactor authentication method. It improves security because it requires more than just a password to log in, making passwords less important.
The benefits of using biometrics instead of passwords are better security, a better user experience, a lower chance of problems caused by passwords, and stronger authentication. Companies make their authentication systems much better, reduce their reliance on passwords, and improve their total security by using biometric traits.
10. Enhanced Convenience
Enhanced convenience means that the authentication method has become easier, simpler, and more user-friendly. It means making it easier, faster, and less complicated for people to prove who they are. It makes the user experience smoother and more efficient.
The use of biometric identification makes things easier to do. Biometric traits, such as a person’s fingerprints, face, eye, or voice, are used to make identity verification simple and easy to use. People do not have to use passwords or PINs to prove they are who they say they are. Instead, they use their unique biological traits.
Biometrics makes things easier because it does not have to remember passwords. Users no longer have to remember complicated passwords or deal with the hassle of having to change their passwords. People easily prove their identity with biometric authentication by showing their biometric traits. It saves time and reduces stress.
The user’s experience is made easier with biometric identification. The process is simple and easy to understand because users use common biometric traits to sign in. The process of proving the person is done in seconds, making it quick and easy whether it is a quick scan of a fingerprint, a quick look at a face, or a spoken phrase.
Biometric authentication is built into many products and programs, making it easy for many people to use. Biometric authentication is built into anything from smartphones and tablets to computers, access control systems, and online platforms. It makes it easy for people to prove who they are in different settings.
There are many ways that fingerprints make things easier. Biometric authentication saves time because it takes less time to prove who the person is. The simpler user experience gets rid of the need to remember complicated passwords or take extra steps. It makes the authentication process easier and more focused on the user. Biometrics are easy to use and do not require much work from the user. It makes them useful for people with different levels of technical knowledge. The seamless integration of biometric identification into current systems and applications provides a unified authentication experience, which makes things even easier.
Biometric authentication makes things easier by getting rid of the need for passwords, making the user experience simpler, making verification fast and easy, and enables people to use the same identification method across platforms and devices. Biometrics makes life easier by saving time, making things easier for the user, being easy to use, and fitting in with everything else. Biometrics helps make the user experience smoother and more fun by making authentication more efficient and easy to use.
What Are the Challenges of A Biometric System?
Listed below are the challenges of a Biometric System.
- Precision and Reliability: Biometric systems must match and store biometric data with a high level of precision and reliability. The accuracy and reliability of the system are affected by things like the surroundings, differences in biometric traits, and injuries or changes to biometric traits.
- Privacy and data protection: Biometric data is very sensitive because it is directly linked to a person’s unique identity. It is important to take the right steps to protect privacy and data to keep biometric information safe from illegal access, misuse, or data breaches.
- Template Storage and Management: Biometric systems use biometric data to make templates or other models that are used to compare and identify people. It is significant to store and handle the templates in a way that is both efficient and safe to keep the system running well and protect people’s privacy.
- Costs and Infrastructure: Setting up a biometric system takes a lot of money to buy hardware, and software, and build the right infrastructure. Organizations need to think about how much it cost to buy, set up, and manage the system, as well as make sure it works with their existing infrastructure.
- Interoperability and Standardization: Biometric systems need to work with other systems and devices and be compatible with them. It makes sure that they are used on different platforms and settings without any problems. Standardizing the formats, protocols, and interfaces for biometric data is important to allow for interoperability and avoid being locked into one provider.
- Acceptance and Use by Users: Getting users to accept and use biometric systems are hard. Users’ acceptance and willingness to use biometric authentication are affected by things like privacy worries, cultural beliefs, and not being familiar with the technology.
- Spoofing and Presentation Attacks: An imposter tries to trick a biometric system by showing it fake or changed biometric traits. It is called spoofing or presentation. Biometric systems must use strong anti-spoofing methods to find and stop the threats.
- Ethical and Legal Considerations: The gathering and use of biometric data raises ethical and legal questions. It is important to follow data security rules, get informed consent, and be clear about how biometric information is used for ethical and legal practices.
- Changes in Biometric Traits: Biometric traits change over time because of things like getting older, getting hurt, or getting medical care. Biometric systems must keep up with the changes and make sure that they recognize and verify people accurately over time.
- Scalability and performance: Biometric systems must grow to handle more work and keep their performance. It is important to make sure that the system is scalable, reliable, and quick to respond as the number of users and activities grows.

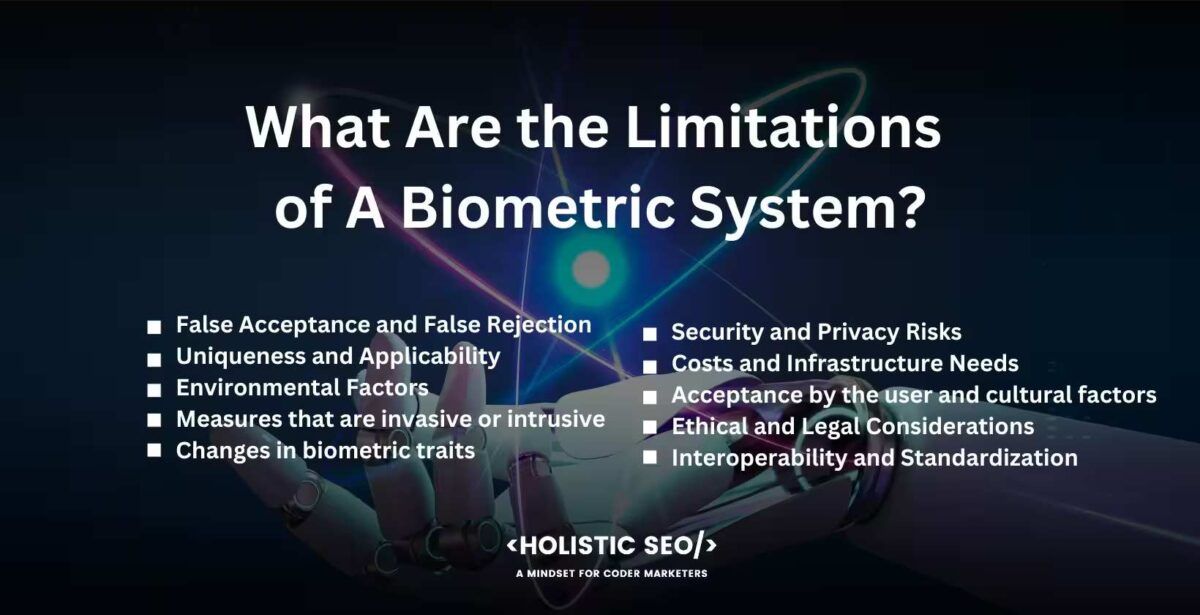
What Are the Limitations of A Biometric System?
Listed below are the limitations of a biometric system.
- False Acceptance and False Rejection: Biometric systems have false acceptance, where an unauthorized person is mistakenly marked as an authorized user, or false rejection, where an authorized user is not recognized by the system. The mistakes are caused by things like differences in biometric traits, changes in the surroundings, or bad data collection.
- Uniqueness and Applicability: Not all biometric traits are fully unique or used everywhere. There is a chance that two people have the same biometric traits, especially when it comes to certain body traits. Some people have diseases or accidents that make it hard to use certain biometric traits to identify them.
- Environmental Factors: Lighting, temperature, and humidity all have an effect on biometric systems. The quality of biological data is affected by things like bad lighting or extreme weather, which make it less accurate and reliable.
- Measures that are invasive or intrusive: Some biometric modes, like recognizing DNA or veins, require invasive or intrusive measures to get the data. It raises questions about privacy, user safety, and how well it is accepted by users.
- Changes in biometric traits: Age, accidents, medical treatments, and other things cause biometric traits to change over time. The changes impact how accurate and reliable biometric recognition is, so systems need to account for them and put in place ways to update biometric models.
- Security and Privacy Risks: Biometric information is very personal and poses security and privacy risks. Biometric information needs to be stored, sent and handled securely to avoid unauthorized access, data breaches, and identity theft.
- Costs and Infrastructure Needs: Setting up a biometric system cost a lot, especially if one has to buy biometric devices, upgrade infrastructure, integrate the system, and keep it running. Consider carefully how much it cost to set up and run a fingerprint system.
- Acceptance by the user and cultural factors: Acceptance by the user and cultural factors affect how widely biometric systems are used and how well they work. People’s willingness to use biometric authentication is influenced by their cultural views, their personal preferences, and their worries about privacy.
- Ethical and Legal Considerations: The gathering, storage, and use of biometric data raise ethical and legal questions. It is important to follow privacy laws, get informed permission, protect data, and be clear about how biometric information is used to keep doing things in an ethical and legal way.
- Interoperability and Standardization: It is hard to get different fingerprint systems and technologies to work together and follow the same rules. It makes it harder to connect to and work with other systems and devices if there are not any standard forms, protocols, or interfaces.
Can Biometric Data Be Stolen or Forged?
Yes, biometric data is subject to being stolen or forged. It is not completely safe from risks and threats, even though biometric authentication makes things safer and more accurate. One worry is the possibility of data breaches, which happen when biometric data is kept insecurely or sent without the right encryption and accessed by unauthorized people or stolen.
The biometric information is reverse-engineered or put back together if the biometric models, which are made from the original data, are lost or stolen. It leads to the creation of fake biometric data that looks like the traits of a real person. Presentation attacks are another risk. They happen when unauthorized people try to trick the system by showing it altered or fake biometric traits, like fingerprints or photos that have been copied.
Repeated attacks and faking or changing biometric data are dangers that need to be dealt with. It is important to remember that biometric traits are unique and hard to copy, which makes them better than traditional methods of identification, even though there are risks.
Strong security measures, such as safe data storage, encryption, anti-spoofing methods, and following privacy laws, help reduce the risks that come with biometric data that have been stolen or faked. Biometric systems offer a better level of security and accuracy for authentication when they are set up and managed well.
How Are Biometrics Used?
Listed below are the ways how biometrics are used.
- The first way is that biometrics are often used to control who gets into buildings, offices, and other physical places. Biometric traits, like fingerprints or face recognition, are used to let people in or keep them out.
- The second way is that biometrics are used to check a person’s identity in many situations, such as airport security checks, border control, and banking transactions. Biometric data is compared against stored templates or databases to authenticate individuals’ identities.
- The third way is that biometrics are being used more prevalent in smartphones and other mobile devices to verify who is using them. People unlock their devices, approve transactions, or get private information by using things like fingerprint sensors, facial recognition, or iris scanning.
- The fourth way is that biometrics are increasingly used in the financial sector to make transactions more safe. Biometric authentication is used for online banking, mobile payments, and ATM transfers. It makes it safer and less likely that someone try to steal the money.
- The fifth way is that biometrics are used in healthcare to identify patients, keep medical data safe, and make sure that medicines are given correctly. Biometric recognition helps make sure that people do not mix up their identities and makes patients safer.
- The sixth way is that biometrics are used a lot at border control checkpoints and during the immigration process to confirm the identities of travelers, track trends of immigration, and improve security.
- The seventh way is that law enforcement agencies use biometrics to identify criminals, such as by matching fingerprints, recognizing faces, or analyzing DNA. Biometric information help solve crimes, find suspects, and find out more about what happened.
- The eighth way is that biometrics are used in workforce management tools to keep accurate records of when employees are present. Fingerprint scanners or facial recognition systems make sure that time is kept accurately and stop people from stealing time.
- The ninth way is that biometrics are built into surveillance systems to make them more secure and allow for real-time tracking. For example, face recognition technology match faces against watch lists or databases to help find threats or people of interest.
- The last way is that biometrics are used in personal devices and apps to verify the user and protect their info. People use biometric features to protect their devices, lock applications, or verify purchases.
How Is Facial Recognition Used in Biometrics?
Biometric technology called “facial recognition” is used to analyze and recognize people based on their faces. It is used in many areas to help with identification, authentication, and security.
Face recognition technology works by comparing a person’s unique facial features to a library of stored “facial templates” and finding a match. It lets people be identified by matching their facial features to those already on file. Face recognition is used in police investigations, access control systems, border control checkpoints, and other places where correct identification is important.
Face recognition is used for user authentication, which lets people use their faces to get into systems, gadgets, or programs. It is now a common function on smartphones, tablets, laptops, and other devices. Users simply show their faces to unlock their devices or approve transactions. It is a quick and safe way to prove an identity.
Facial recognition technology is used in monitoring and security systems to make them safer. Faces are picked up by cameras, and the technology compares them in real-time to watch lists or files. It makes it easy to find potential threats or people of interest quickly, which lets people move quickly and stops security breaches.
Face recognition technology is used to customize how users interact with different apps. It makes content, ads, or suggestions that are more relevant to each person by looking at a user’s facial expressions, feelings, or demographic information. It makes users more engaged, improves the customer experience, and makes it sell to specific groups.
Facial recognition is used in systems that keep track of attendance and time at work. It correctly keeps track of employee presence by taking a picture of their faces when they clock in and out. It helps stop people from stealing time and makes sure that the staff is managed well.
Face recognition technology is a big part of keeping people safe and helping the police do their jobs. It helps find suspects, find people who have gone missing, or stop fake activities. Face recognition is used by law enforcement to match faces from crime scenes or surveillance videos to criminal records. It helps with investigations and makes things safer.
Face recognition is used a lot to check people’s identities at the gate and during the immigration process. It compares the faces of travelers to those in biometric databases. It makes sure that travel papers are correct and improves security at the border.
There are some worries about privacy, accuracy, and biases, even though face recognition has many benefits. It needs to put in place strong security measures, make sure there is transparency and consent, and deal with worries about data privacy and protection to use facial recognition technology in a responsible and ethical way.
Can Iris Recognition Be Fooled by Contact Lenses?
Yes, iris recognition is fooled by contact lenses under certain circumstances. Iris recognition technology is generally considered to be highly accurate and secure, as the iris pattern is unique to each individual. However, contact lenses affect the accuracy of iris recognition systems.
Iris recognition works by taking high-resolution pictures of the iris, which have patterns that are used to identify the person. The patterns do not change much over time and stay fixed. Wearing contact lenses change the way the eye looks, which affects how well the recognition process works.
Changes are made to the pattern of the iris by wearing colored or patterned contact lenses, especially if the pattern covers a large part of the eye. Artificial patterns or colors on the lenses add more details or hide the natural patterns of the iris, which cause differences between the image recorded, and the template saved in the system’s database. It leads to false rejection or false acceptance mistakes, in which people who do not wear contact lenses are wrongly identified as people who do wear them.
Iris recognition is hard to do with some kinds of contact lenses, like those with reflective coatings or certain optical qualities. The lenses reflect or distort light, which makes the picture quality bad or makes the iris image look wavy. The system has trouble getting the unique parts of the eye to match and identify the person.
It is important to know that current iris recognition systems are made to work with some of the differences that contact lenses cause. They often use algorithms and techniques, like picture normalization, image enhancement, and liveness detection, to make up for the effects of contact lenses. Liveness detection helps figure out if the iris being recorded is from a real person or if it is an attempt to fake an iris. It is done by wearing contact lenses or showing a fake image.
It is essential to come up with best practices and rules for dealing with contact lenses to make eye recognition systems more reliable and accurate. It means adding more verification methods or protocols, like asking people to take out their contact lenses during the authentication process, using multi-modal biometric systems that combine iris recognition with other modalities, or using advanced algorithms to detect and counteract the effect of contact lenses on the recognition process.
Contact lenses make eye recognition systems less accurate, but technology is always getting better to deal with such problems. Biometric systems that use eye recognition try to adapt to different situations and make themselves less likely to be fooled, even if contact lenses are used.
How Is Fingerprint Recognition Used in Biometrics?
Fingerprint recognition is a widely used biometric technology that is employed for identification and authentication purposes. It checks a person’s identity by looking at the unique patterns and ridges on their fingers and matching them up.
User registration is one of the main ways fingerprint recognition is used. It lets people access systems, devices, or apps safely by scanning their fingerprints and comparing them to templates that have been saved. It is clear in smartphones, laptops, access control systems, and other devices with fingerprint readers that make user authentication easy and safe.
Fingerprint recognition is an important part of police work and evidence. Law enforcement uses fingerprint files to match fingerprints found at crime scenes with their own records to find out who did it. Fingerprints are useful in criminal cases because they are unique and stay the same.
Fingerprint recognition is used a lot for border control and visa procedures. Travelers have to give their fingerprints at immigration checkpoints, which are then checked against databases to make sure they are who they say they are and that their travel papers are real.
Fingerprint recognition is often used to keep track of time and attendance. Workforce management systems use fingerprint scanning to keep track of when workers clock in and out. It keeps time theft from happening and makes sure attendance records are accurate.
Fingerprint recognition has been used to make financial activities more secure. People approve payments, get into their online bank accounts, or do other financial transactions by scanning their fingerprints. It makes the system more secure and reduces the risk of fraud.
Fingerprint recognition is used a lot in systems that control physical entry. Fingerprint-based access control is used by organizations and buildings to allow or reject an entry based on authorized fingerprints. It makes sure that only authorized people get into restricted areas.
Fingerprint recognition is used in health care to identify patients and keep track of their records. Matching fingerprints to patient data improves accuracy, cuts down on mistakes, and makes sure that the right care is given.
Fingerprint recognition is built into personal gadgets and apps to make them safer and more private. Fingerprint sensors are used in smartphones, tablets, and other devices to make it easy for people to unlock their devices, protect private information, and authorize transactions.
Fingerprint recognition is used to check a person’s identity and make sure they are who they say they are when using e-government services. It lets people access government websites, sign papers digitally, and do secure online transactions.
Fingerprint recognition has become an important part of biometric systems in many businesses and applications because it is unique, easy to use, and widely used. It makes identifying and authenticating people easier, safer, and faster, and it offers reliable and generally accepted biometric authentication.
How Does Voice Recognition Work in Biometric Authentication?
Voice recognition work in biometric authentication by identifying individuals based on their unique voice characteristics. Voice enrollment is the first step to work in biometrics. It is where a person’s voice samples are taken by having them say certain words or sentences over and over again. The voice samples are used to make a unique voiceprint that shows the person’s unique vocal traits. The voiceprint is a mathematical representation of the person’s voice. It includes things like pitch, rhythm, frequency, and length.
The person’s voice is recorded again and compared to the voiceprint that has been saved during the verification process. Advanced algorithms look at the data about the voice, pull out features, and turn those features into a digital image. Using pattern matching or machine learning, the recorded voice is then compared to the voiceprint that was already stored. It compares the captured voice to the enrolled voiceprint to see how close they are. The result is either a verification or an identification.
The system checks to see if the voice it has recorded fits the voiceprint of a certain person in verification mode. The mode is often used when the person’s name is already known, like when they are logging into a secure system or giving permission for a transaction. The system looks through all the voiceprints it has stored to figure out who is talking in recognition mode. The mode is useful when the speaker’s name is unknown and a bigger pool of possible matches needs to be searched.
The system decides with a certain amount of confidence if the voice that was recorded matches the voiceprint that was stored based on the results of the comparison. Access is given to the system, device, or service that was asked for if the match is good enough. Entry is denied, or more ways of proving the identity is needed if the match is not good enough.
Voice recognition is helpful because it is easy to use, does not get in the way, and is widely accepted. It is used for phone-based authentication, call center verification, devices that are managed by voice, and transactions that are done by voice. Accuracy is affected by things like background noise, voice quality, or changes in the speaker’s voice. Voice recognition is a useful biometric authentication method because machine learning algorithms and voice recognition technology are always being improved to make them more accurate and solve the problems.
How Does Gait Recognition Used in Biometrics?
Gait recognition is a type of biometric technology that uses a person’s unique way of walking to identify and verify that person. It involves looking at the length of a person’s steps, how fast they walk, how their arms swing, and how their body is positioned.
One of the main ways that gait recognition is used is in surveillance devices to identify and keep track of people. Gait recognition algorithms match a person’s walking pattern with a template to recognize or track them. They do it by looking at the walking patterns that are captured on video. It is helpful in situations where standard ways of identifying someone are not possible or work.
Gait recognition is used in physical space entry control systems. Specialized sensors or cameras record how people walk, and entry is given or taken away based on how the patterns are analyzed. The method is especially helpful in secure or restricted places where traditional ways of identifying people are not possible or are inconvenient.
Gait recognition is used in forensics and law enforcement to help analyze surveillance footage or video proof to identify people based on the way they walk. The feature helps police find criminals and track them down, and it is used as evidence in court.
Gait recognition technology help with health monitoring by looking at a person’s walking movements all the time. It tells if a person walking is not normal, which is a sign of health problems or accidents. The app is used in healthcare situations to find mobility-related problems early or track the progress of rehabilitation.
Gait detection is part of systems that use ambient intelligence. It makes to provide personalized services and changes the environment to meet the needs of each person based on the way they walk. It is through studying the way people walk in a smart environment, like a smart home or office.
Gait recognition is used as an extra factor in biometric identification systems, along with other biometric methods. Get more accurate and secure identity verification when combining technologies like fingerprint or face recognition with gait recognition.
Gait recognition has some advantages, like not being intrusive and being able to tell who someone is from a distance. However, there are some issues to think about, like how walking speed, clothes, carrying things, or shoes change gait patterns. People who have trouble moving or who use gadgets to help them not be good candidates for gait recognition.
Gait recognition systems are getting more accurate and reliable as computer vision, machine learning, and sensor technologies keep getting better. Gait recognition adds an extra layer of identification and authentication when combined with other biometric and security technologies. It helps make security measures stronger and gives users a more personalized experience in different apps.
How Does Palmprint Recognition Used in Biometrics?
Palmprint recognition is a biometric device that uses the unique patterns and features on a person’s palm to identify them. User identification is one of the main ways that palmprint recognition is used. The system takes a palmprint and matches it to stored templates to make sure the person is who they say they are by scanning a person’s palm. The way of authentication is often used in access control systems, secure buildings, and other places where people need to be verified before they use a device.
There are times when forensic investigations use palmprint identification. Palmprints found at crime scenes compared to records of known people to find out who the suspects are. The unique designs on the palm are used as strong evidence in court.
Palmprint recognition is used at the gate and in the immigration process. Travelers have their palms scanned, and the captured palmprints are compared against existing records to verify their identities and ensure the authenticity of travel documents.
Palmprint recognition is used to verify the owner of personal devices like smartphones, tablets, and laptops. Users open their devices or approve transactions by scanning their palms. It adds another layer of security.
Systems that keep track of attendance and time use palmprint identification. Employees clock in and out by having their palms scanned. It keeps accurate records of their work hours and prevents time theft.
Financial services are increasingly adopting palmprint recognition for secure transactions. Individuals authorize payments or access their financial accounts by scanning their palms, enhancing security and reducing the risk of fraud.
Health tracking are done with the help of palmprint recognition. It finds out if someone has a certain medical condition or to spot early warning signs of diseases that change the way the palm looks by looking at palmprints.
Palmprint recognition has benefits like being unique, staying the same over time, and being easy to get. Palmprint recognition is a reliable biometric technology because it is hard to fake or copy the designs on the palm. Palmprint recognition systems are getting better as image processing, pattern recognition, and machine learning keep getting better. It makes them more accurate and useful in many biometric uses.
How Are Biometrics Used in Access Control Systems?
Biometrics are a big part of entry control systems and make them safer and easier to use in many places. They are usually used in several ways when biometrics are used in access control systems. First, people who want to use the system have their fingerprints, iris patterns, or palmprints taken and saved as models in the system’s database.
They show their biometric trait to the system to verify their identity when people try to get into a secure place or use a secure resource. Devices like fingerprint scanners, iris scanners, and palmprint readers are used to get biometric information at the point of entry. The collected data is then compared to the templates that were signed up for, and entry is given if there is a match within an acceptable range. Entry is denied if there is no match or if the match is not close enough to the threshold.
Biometric access control systems often use multifactor identification to improve security. It is done by combining the biometric trait with other credentials like PINs, passwords, or proximity cards, which add another layer of proof.
Time and attendance tracking is done with biometric access control tools as well. The systems correctly record when employees clock in and out, which makes time theft and buddy punching less likely to happen by combining biometric authentication with time-tracking.
Biometric entry control systems keep audit trails and make reports to help with security and compliance. Access events, such as successful and unsuccessful efforts at authentication, are recorded along with details about the user and the time. The audit trails make it easier to look at entry patterns, find security holes, and follow the rules.
Biometric access control systems are connected to other security systems, like surveillance cameras, alarms, or guest management systems, for a complete security solution. Access events set off actions or alerts that is monitored and responded to in real-time.
Biometric entry control systems are getting the ability to let people in from afar as technology gets better. Users use their biological traits to safely access resources or facilities from far away, either through dedicated mobile apps or web-based platforms. It makes access control easy and safe in many situations.
Biometric access control systems offer more security, less dependence on traditional credentials, a better user experience, and more accountability. The systems provide a strong and easy way to control access to physical spaces, resources, or digital systems by using unique physical or behavioral traits, which improves total security and operational efficiency.
What Are the Ethical Implications of Using Biometrics for Identification in Ai?
Using biometrics for identification in AI has important ethical issues that need to be thought carefully. Biometric data is personal and sensitive, privacy and data security are important. Have to follow strict privacy rules, secure it, and only use it for what it was made for to keep biometric information safe. People must know how data is collected and used through clear rules and ways to give informed consent.
Informed consent is significant because it makes sure that people have the right to say “yes” before their personal data is taken and used. Data usage, access, and possible risks need to be talked about in a clear way. People must choose what to do with their biometric information and have real power over it.
Accuracy and lack of bias are essential social concerns. Biometric systems must be accurate and free of biases, since mistakes or biases lead to false identifications or bans. Biometric systems must be kept honest by fixing algorithmic flaws and making sure they are fair, transparent, and do not discriminate.
The ability to withdraw consent and the ability to keep records are important. People must change their minds and ask that their genetic data be deleted. Clear rules about how long to keep data and how to delete it safely are critical for valuing people’s choices and keeping their privacy safe.
Widespread use of biometric identification systems make people worry about too much monitoring and violate their right to privacy. It is significant to find a balance between security and individual freedoms to avoid too much monitoring and protect privacy.
Another ethical thing to think about is how to stop injustice and negative social effects. Discrimination and social biases must not make worse by biometric technology to avoid too much monitoring and protect privacy. It is important to make sure that the use of biometrics does not hurt disadvantaged groups more than others or cause people to be left out of society.
Transparency and being responsible are very essential. The creation and use of biometric identification systems must be open, and there are clear ways to hold people accountable. It is critical to be open about methods, data sources, and how decisions are made. Independent audits and review help make sure that rules and standards of ethics are followed.
It needs a strong ethical framework that protects the rights, freedom, and fairness of each person to use biometrics for identification in AI. It is essential to understand ethical implications with biometrics to find a balance between the benefits and the possible risks to make sure that biometric technologies are used in a way that is fair and protects people’s rights and well-being.
What Are the Legal Frameworks and Regulations Surrounding the Use of Biometrics?
The use of biometrics is subject to various legal frameworks and regulations that aim to protect individual privacy, ensure data security, and promote the responsible use of biometric technologies. The General Data Security Regulation (GDPR) is a law in the European Union (EU) that covers all aspects of data security. It has strict rules about how personal data, such as biometric data, must be collected, processed, and stored. It sets up rules like “data minimization,” “purpose limitation,” and “informed consent,” and organizations must make sure that biometric data is handled legally, that information is given clearly, and that the right security measures are taken to protect it.
The California Consumer Privacy Act (CCPA) is a law that protects the privacy of California residents whose personal information is collected and used by companies. It gives the same kinds of protections as the GDPR. People have the right to know what personal information is being gathered, to stop it from being sold, and to have their data deleted. Under the CCPA, biometric information is considered to be private personal information.
Several U.S. states, like Illinois, Texas, and Washington, have passed Biometric Information Privacy Acts (BIPAs) to control how biometric data is collected, used, and kept. The rules say that it has to get informed consent, keep data safe, and give people certain rights about their biometric information.
The Personal Information Protection and Electronic Documents Act (PIPEDA) is the law in Canada that says how personal information, including biometric data, is collected, used, and shared. Organizations must get people’s permission, keep information safe, and let people see their own information.
The Health Insurance Portability and Accountability Act (HIPAA) protects private health information in the United States, which include biometric data gathered in healthcare settings. It sets rules about how health information is used and shared and how it must be kept safe and private.
International standards like ISO/IEC 19794, ISO/IEC 24745, and ISO/IEC 29100 give rules for protecting biometric data. The standards cover things like data structure, encryption, and privacy principles.
There are rules that are specific to that sector in some businesses. For example, the Payment Card Industry Data Security Standard (PCI DSS) tells payment systems how to keep fingerprint data safe.
Organizations that use fingerprints must make sure they follow all the laws and rules. It builds trust, protects people’s rights, and reduces the legal risks that come with using fingerprint technologies. Protect the data, keep the privacy, and get permission to use it in the right way by following the rules. It encourages the responsible and ethical use of fingerprints.
How Are Biometric Systems Evolving, and What Are the Latest Advancements in The Field?
Biometric systems are always getting better at being accurate, safe, and easy to use. There have been a number of improvements in the field in recent years. Deep learning and artificial intelligence (AI) methods have changed biometric systems by making them match and extract features more accurately. It is a big step forward. It has improved performance and cut down on the number of false acceptances and rejections. Another important trend is the use of multi-modal biometrics, which uses multiple biometric traits like face, fingerprint, and eye to improve accuracy and reliability.
Contactless biometrics have gotten a lot of attention because they are clean and easy to use. For example, contactless fingerprint scanners read fingerprints without touching them. Face and iris recognition systems that do not touch the user use infrared or depth-sensing cameras to record biometric information without touching the person. Anti-spoofing and presentation attack-detecting methods have been made to stop attempts at fraud. The methods use liveness detection algorithms to make sure that the biometric trait given is real, which makes the system more secure.
Biometrics that use sensors built into smartphones is becoming more common. It makes identification easy and safe. Continuous authentication is a new idea in which biometric traits are checked and watched all the time during a session to look for unusual behavior or unauthorized access. Wearable biometrics have become more common because they let a person keep an eye on their heart rate or blood pressure at all times.
Cloud-based biometric systems use the ability to grow and the computing power of cloud technology to match and store large amounts of biometric data. It allows for easy deployment, centralized control, and collaboration between different places. There is a growing focus on explainable and transparent biometrics, aiming to provide insights into the decision-making process of biometric algorithms.
Advances in privacy-protecting techniques aim to keep people’s privacy safe while letting them use fingerprints. Methods like secure multiparty computation, homomorphic encryption, and federated learning make it possible to handle biometric data without exposing or sharing it in its raw form.
The changes to fingerprint systems make them more accurate, safer, and easier to use. Research and development efforts continue to push the limits, making biometric technologies more sturdy, reliable, and flexible for use in fields like security, healthcare, and finance, among others.
- 48 Online Shopping and Consumer Behavior Statistics, Facts and Trends - August 22, 2023
- B2B Marketing Statistics - August 22, 2023
- 38 Podcast Statistics, Facts, and Trends - August 22, 2023